
For some months now, Microsoft has deployed on the Azure platform, Key Vault. This solution gives you the possibility to store, directly on Azure, your passwords, certificates, etc. and to generate/call them through API. Resources can be accessed from Azure Automation, Azure AD and from your custom applications.
You can find the full documentation here: https://docs.microsoft.com/en-us/azure/key-vault/
Regarding the cost, it depends of your use. All details are available here: https://azure.microsoft.com/en-us/pricing/details/key-vault/
Create your first vault
To create your vault, navigate to the marketplace and search Key Vault. Create a new one:
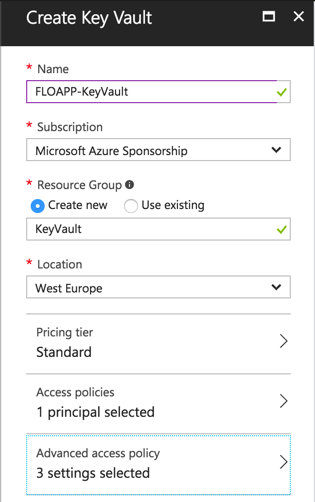
It’ll take a few seconds to deploy the vault. When it’s finished, you should have this:
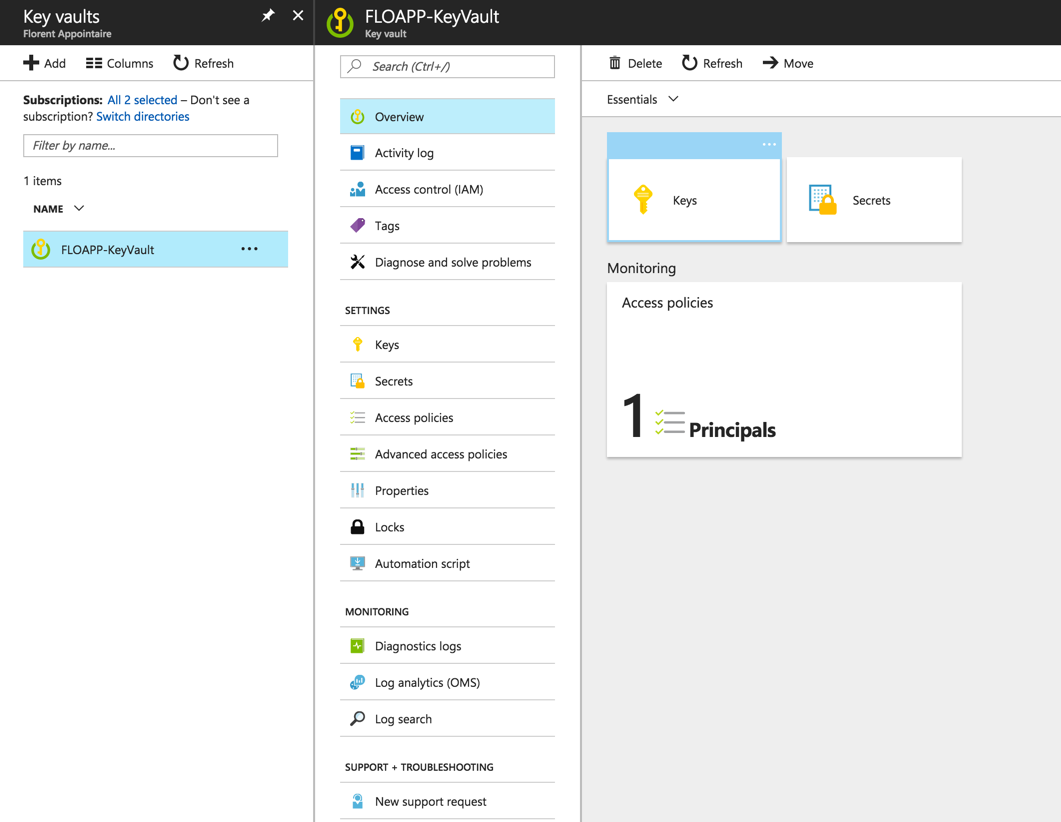
Secrets in Key Vault
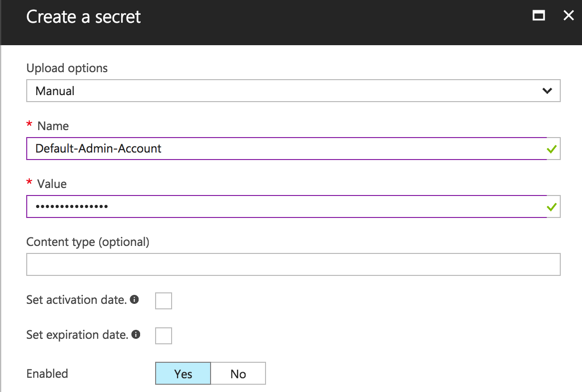
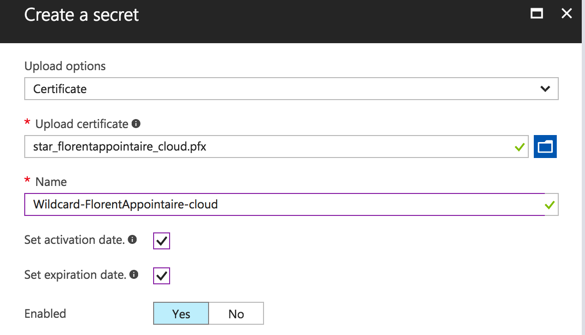
Start by using the Secrets part who give you the possibility to store certificates, but password too. To store a new password, go to Secrets > Add and choose as upload options, Manual. Provide a name (space is not allowed) and value of this password. You can provide an activation date and when this password will expire:
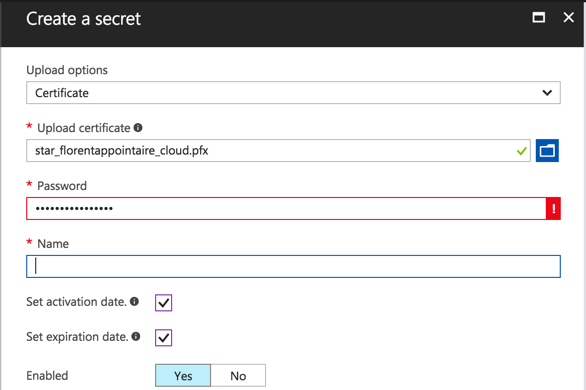
Do the same for the password with extension PFX and provide the password to use this certificate. If the password is not correct, you’ll have an error message:
And with the good password:
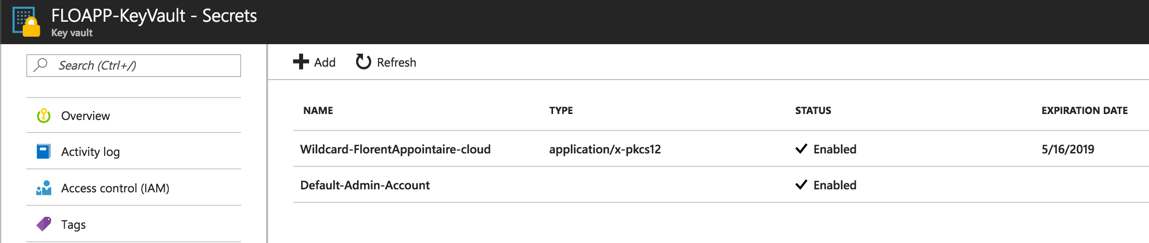
Your 2 resources are now deployed:
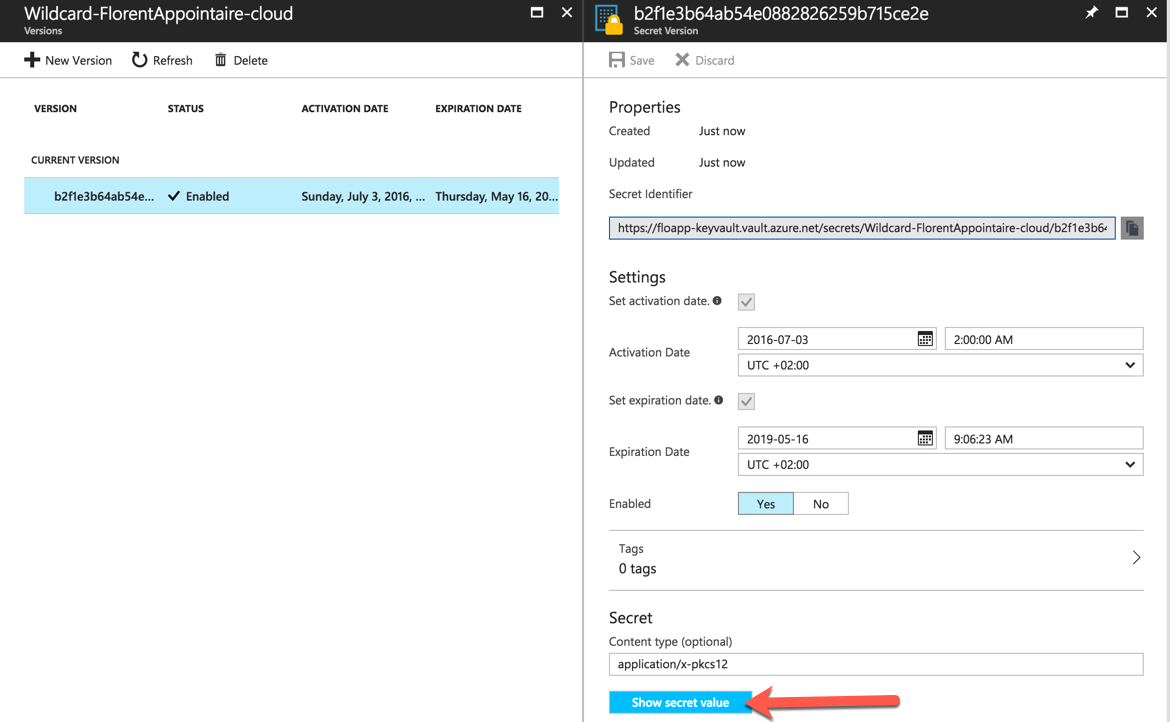
If you want to see what is inside services that you created, just go to the service and click on Show secret value and the value will be displayed:
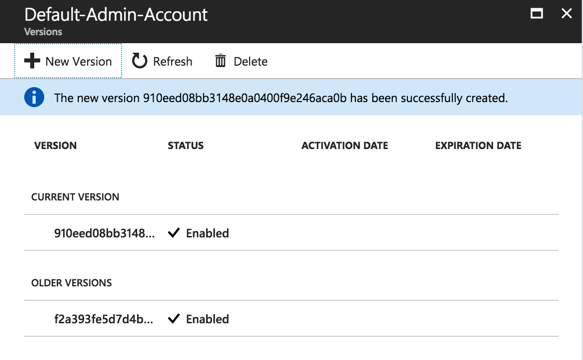
You can have a history of all versions:
Keys in Key Vault
For the Key part, you can create a key that will give you the possibility to:
- Encrypt
- Sign
- Wrap Key
- Decrypt
- Verify
- Unwrap Key
When this key is generated, it will give you the possibility to do the previous operations, by using his Key identifier:
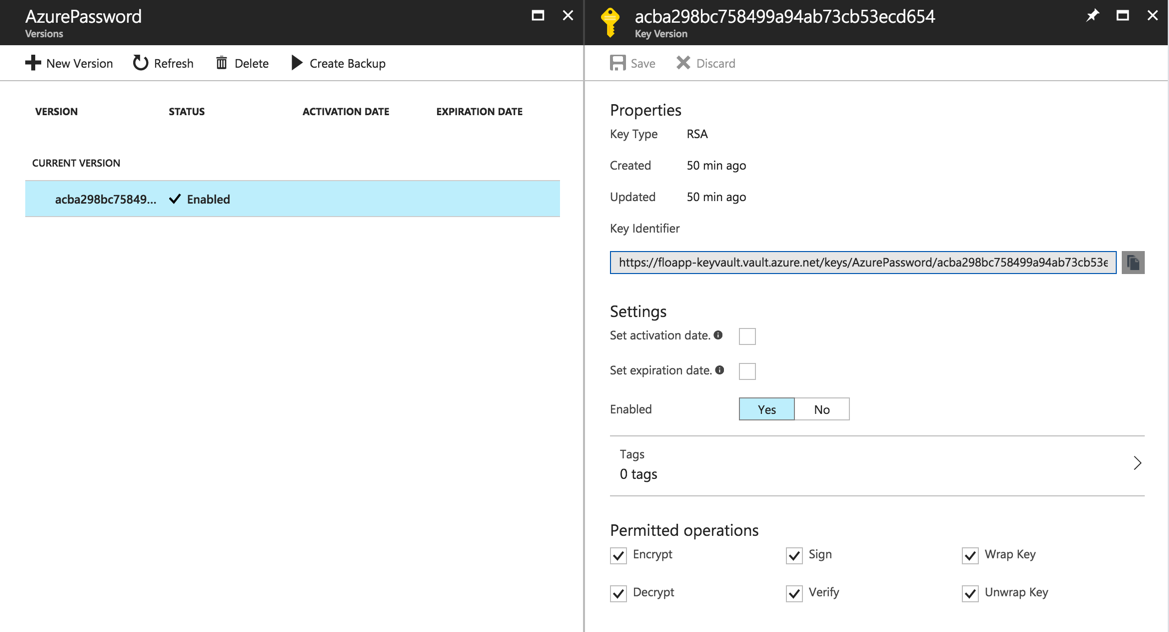
You can use this key from applications, with API calls, or with PowerShell for example.
You can back up these keys, directly from the Azure portal:
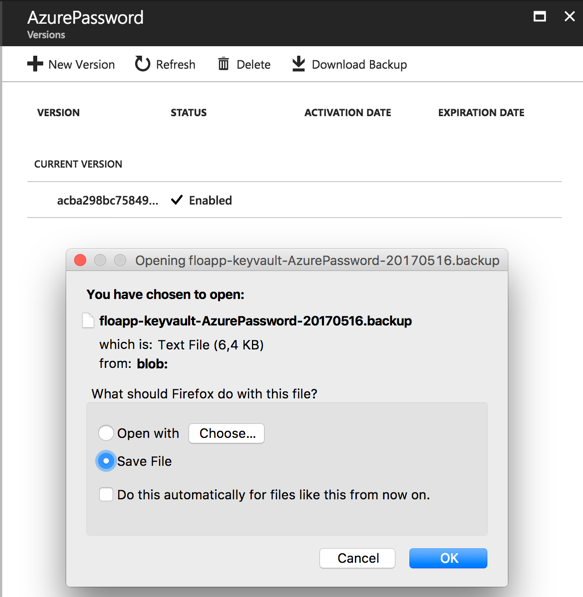
This key can be restored from the Azure portal.
Permissions
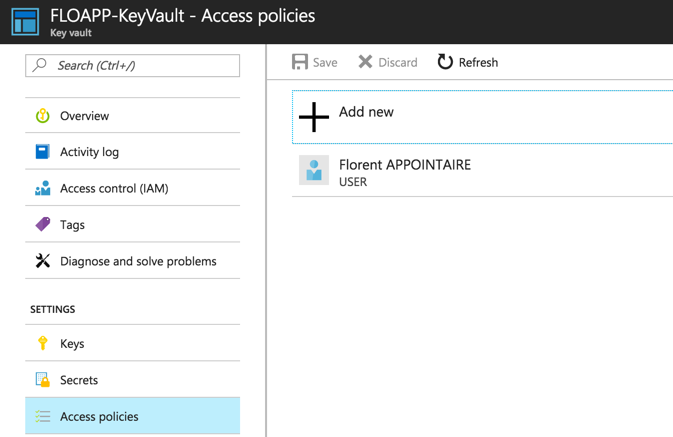
Because some passwords can be critical, you can give them to anybody It’s why you can manage permissions. Click on Add new on Access policies tab:
Select a user to apply for permissions. Be careful, you will give the authorization to all the section and no to one Keys or Secrets that you choose. My user will have only access to Keys:
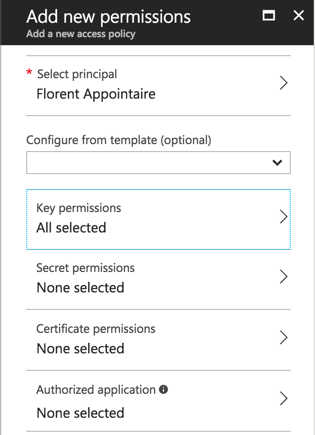
Click on Save and connect to the Azure portal, with the user where you added permissions. Be careful to give Read permissions on the resource group where the Key vault is deployed, otherwise, the user will not be able to see the vault.
Open the Key vault. You will normally have access only to the Keys part, in Read/Write:
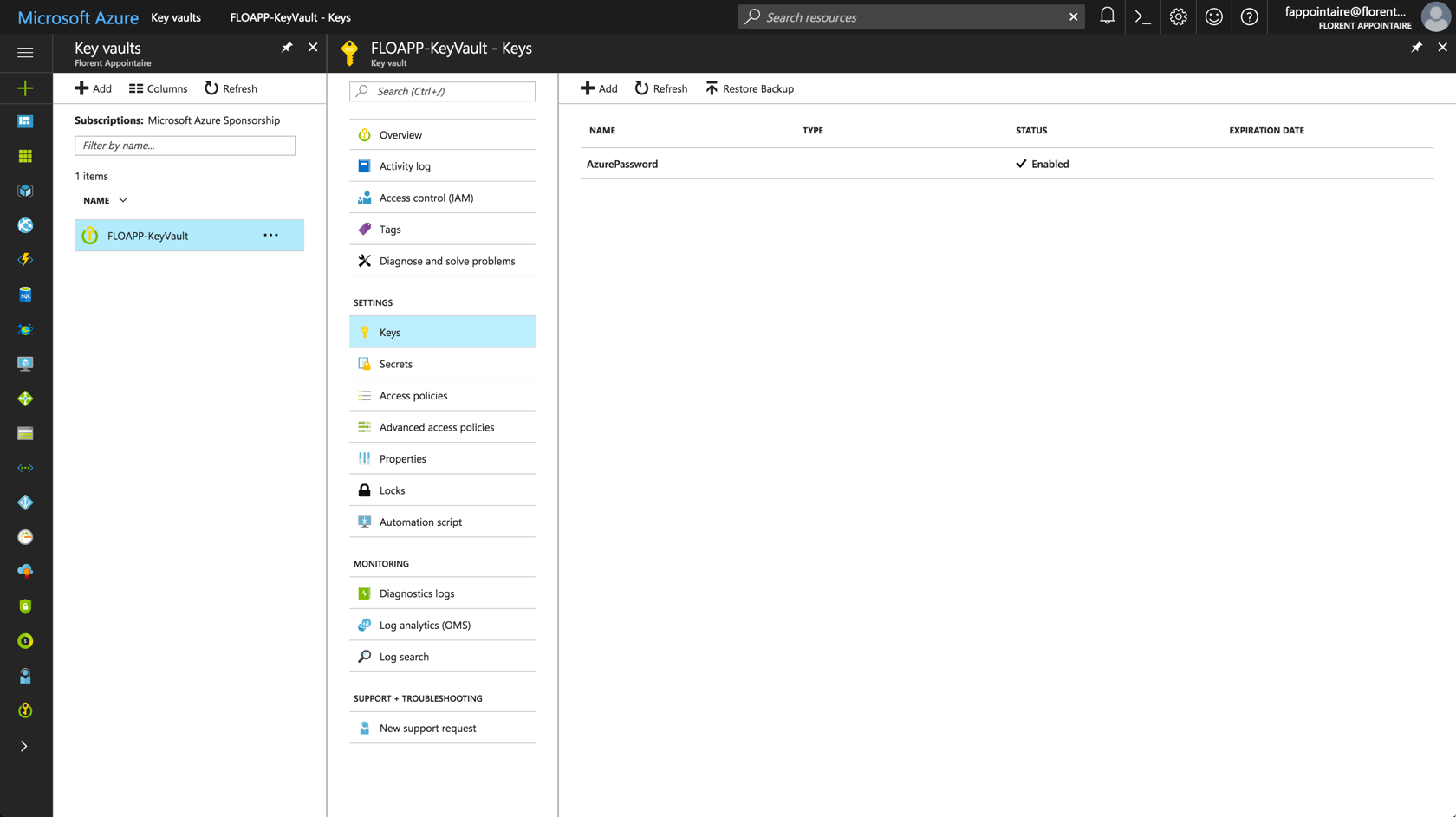
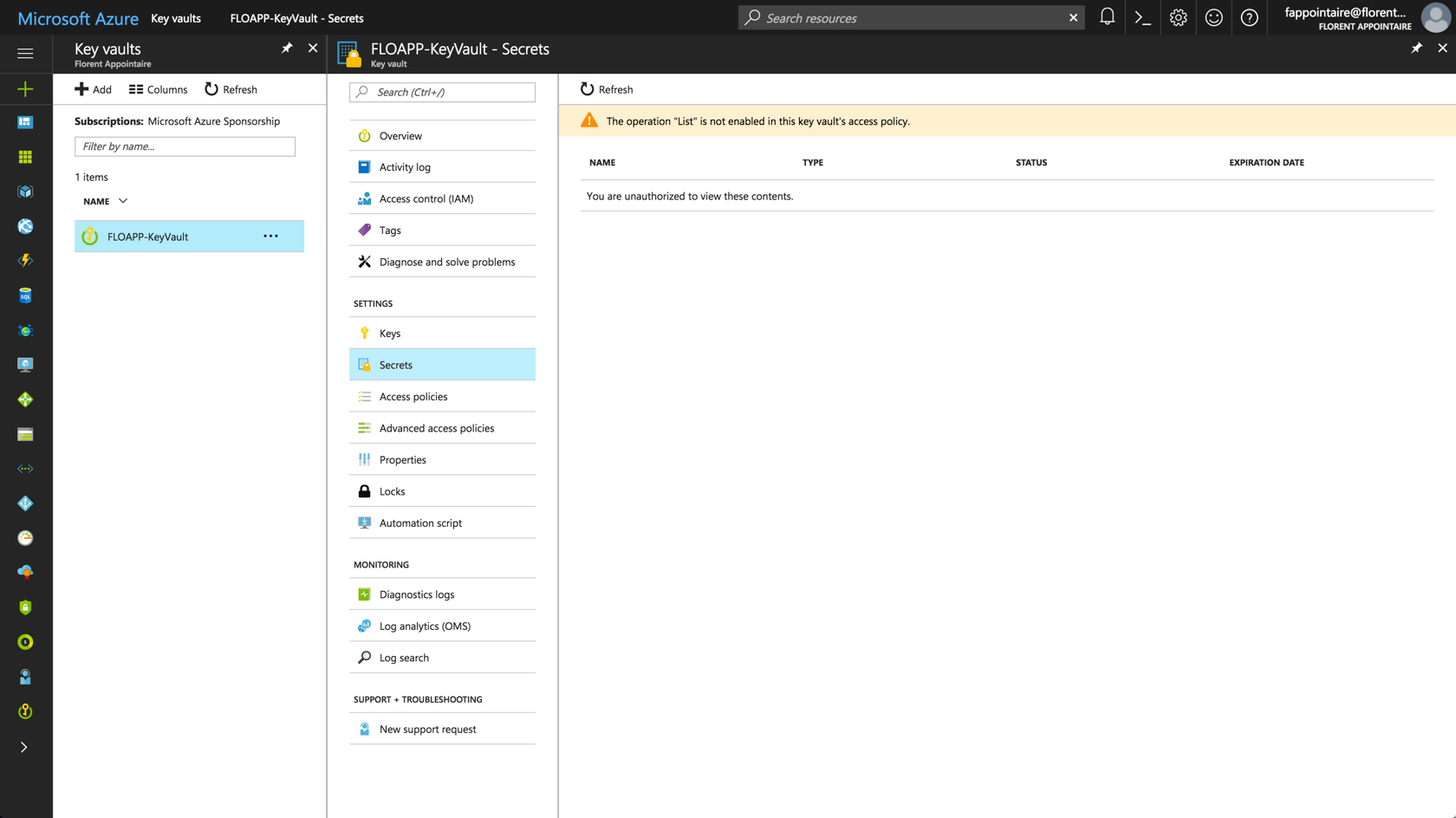
It’s the case. Because I don’t have necessary permissions for the Secrets part, I’ve the following error message:
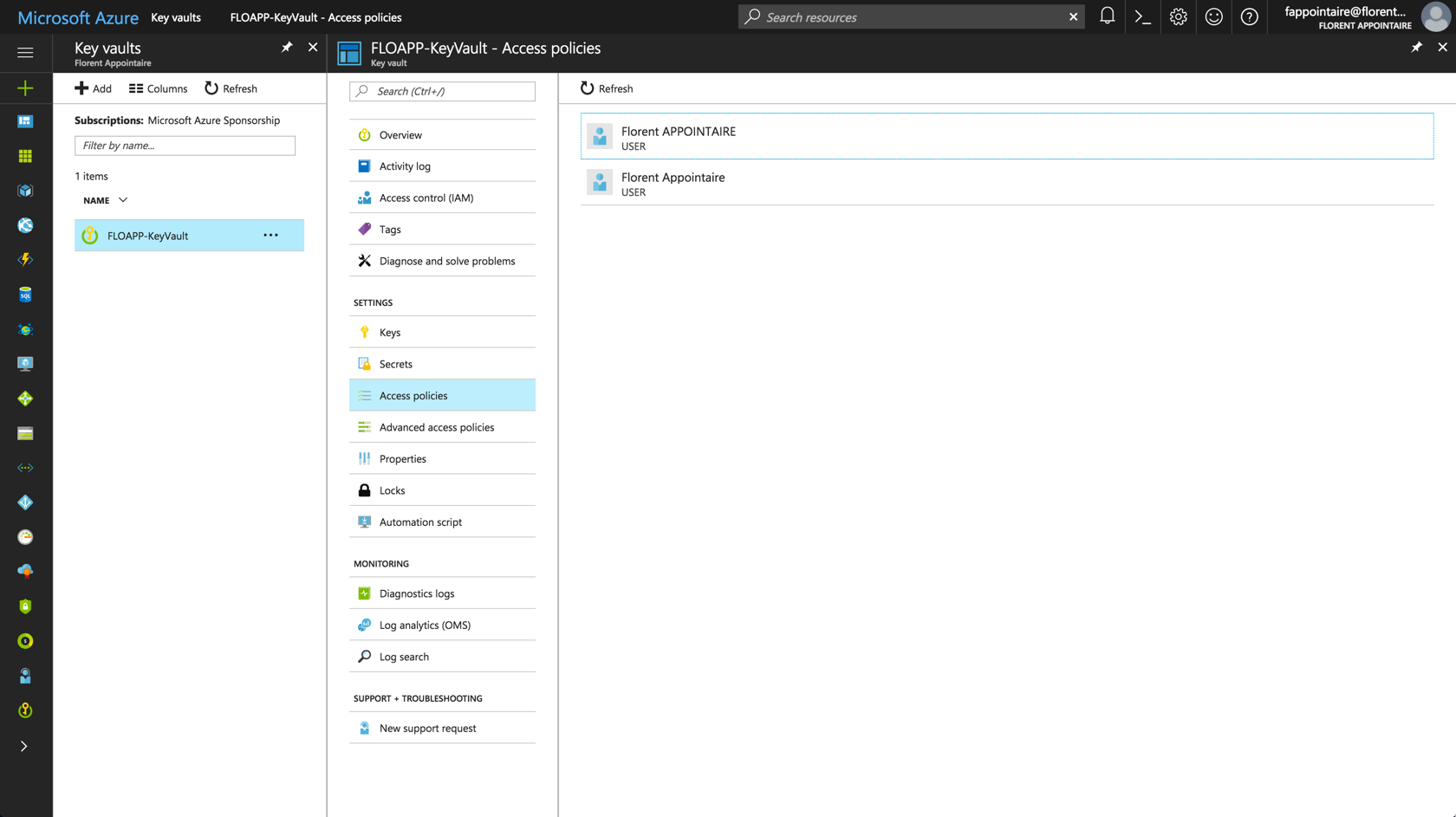
And, I’ve a Read access on policies:
Conclusion
To conclude, this service is here to concurrence software like KeyPass, 1Password, etc. but with more functionalities. In fact, you can call a password from your PowerShell scripts that are stored in the KeyVault and in your applications too. This is very useful to update regularly your password in your enterprise (for security reasons) and without modifying code and so on every time. And the possibility to manage authorizations is a big plus. The price of the service is very low, so why deprive yourself?

Views All Time
1

Views Today
3
The following two tabs change content below.
Filed under:
Software by Florent Appointaire