INTRODUCTION
In the modern world, we no longer go through our daily lives, which often include study and work, without computers. Computers are used everywhere – from schools and educational institutions, to shops and entertainment centers, to the spheres of service and production, to the transportation sector, to the field of medicine, and in accounting and legal organizations. With the growth of the number of computers in our everyday life, we are increasingly confronted with a host of problems related to data storage, particularly protection against viruses, malware, and external intrusions by hackers.
PROBLEM
The increase in the number of workplaces with computers at all enterprises and organizations requires businesses to build up their internal-protection infrastructure and to hire expensive, narrow-profile specialists, tasked with preventing the penetration of viruses and malicious programs, as well as blocking simple attacks by hackers, attacks designed to steal personal, confidential, or commercial information.
How can we protect all computer users, do it right away, and provide protection against all sorts of threats on a huge number of installed computers, units that may require different operating systems, work programs, and different access-rights to the internal network and the Internet?
SOLUTION
AcloudA offers a solution that can not only solve the problems of information security, but also solve another, equally-important problem. Namely, we offer a quick, simple increase in space for any network user, provided not by improving or buying new equipment for each user, but by upgrading the internal server or simply switching to another tariff on a remote or cloud-storage server.
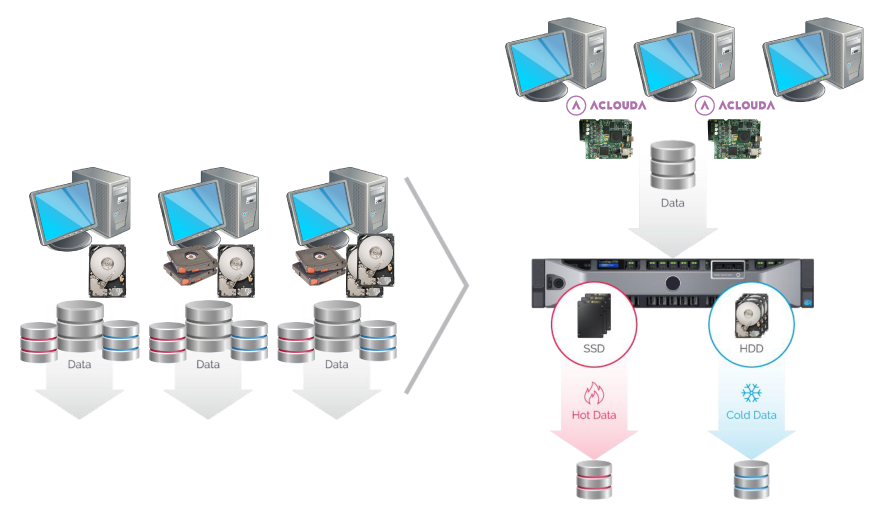
AcloudA provide ability to use one centralized data storage for many different computers
In order to install our device, you must connect it the local network, not the hard drive inside any workstation, and, initially turning to internal, remote, or cloud storage, allocate the required amount of space on the server. The user must then establish an operating-system on the received “hard disk” and complete all remaining steps to ensure that program works (or simply to make an image of an old hard disk and put it into the system). And that’s all! Next, you simply configure the server to create snapshots of all the system images that your users use, a move that offers the ability to restore a workstation that is not infected by the virus of each user.
And, if there is a need in the future to increase the space needed for storing more data for your users, you will not have to buy new ones or improve old workstations, as you may simply allocate more space on the server or purchase equipment (as soon as it is completely filled) only in the server. Further, when using cloud storage, all that needs to be done in the future is to switch to a different payment plan (one that includes a large prepaid storage space).
In addition to the aforementioned features, AcloudA offers a completely new approach to data security, so simple and effective that it literally leaves 0% probability of any intrusion, leaving only the possibility of tracking data from from the cloud to AcloudA. As long as the data is encrypted and the keys are stored in the main infrastructure, no one will be able to pick up keys or intercept any real data. The reason is simple – even if the hacker gets full control over the device itself, there is no way to physically proceed any further.
CONCLUSION
We offer a solution for everyone (from small companies to large organizations and manufacturers), enabling them to efficiently solve emerging problems in the information infrastructure without resorting to large capital investments or serious changes to a well-functioning system. You receive a simple and reliable way to manage and organize your infrastructure, with the option for simple and cheap expansion in the future.
Fill the form below to get Extended version of this Use Case